1H 2025 State of Exploitation Report
Exploitation Trends in the First Half of 2025
Our research analyzes 432 exploited CVEs in the first half of 2025, where nearly one-third of these vulnerabilities were exploited on or before disclosure, demonstrating the persistence of zero-day and one-day exploitation. During this period, threat actor activity shifted, with Russia and Iran showing increased exploitation activity while reports tied to China and North Korea declined. Categories such as CMS platforms, network edge devices, and server software continued to drive mass exploitation, while hardware exploitation also rose.
The report further highlights how delayed NVD analysis leaves defenders exposed, with more than a quarter of new KEVs still awaiting review. With compressed timelines and increasingly sophisticated adversaries, defenders face mounting challenges that demand faster intelligence and more proactive responses.
Our report calls out key findings:
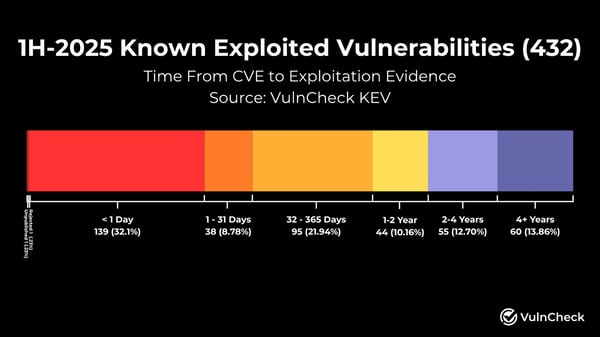
432 CVEs had first-time exploitation evidence in 1H-2025 — a sharp reminder of attackers’ pace.
32.1% of KEVs were exploited on or before disclosure, up from 23.6% in 2024.
Russia and Iran exploitation activity grew, while China and North Korea exploitation dropped.
Proprietary software (CMS, network edge, and server software) remains a larger driver of mass exploitation than open source.
26.9% of KEVs from 1H-2025 are still awaiting NVD analysis — highlighting gaps in timely vulnerability coverage.
Stay ahead of attackers with the latest exploit intelligence from VulnCheck.
Download the full State of Exploitation – 1H 2025 report to see the data, trends, and insights driving today’s threat landscape.